

Please visit http://www.wissh.com for WiSSH, our RDP over SSH client. A secure, easy to use, fast client designed for end users but powerful enough for everyone. The overall design is based on this article but is much more functional.
SSH Tunneling is a wonderful way to grant remote access to your users or your home PC from the office. The technology works as follows: You have a Linux (or other SSH system) server running where port 22 is open to the internet. This is the SSH port, which is secure and encrypted.
Behind this server and on your internal network you have an XP workstation or Windows Terminal Server available for use. This runs the Remote Desktop Connection server on port 3389. This is a great way to remote access your systems. The client is built in on Windows XP and is an ActiveX plug-in on a web page.
Now, from your remote location, you have to connect to that port 3389 on the internal box. Lets say your company has 500 workstations, and each user is allowed to remote control their desktop. You can't have that many systems exposed to the internet. Way too many IP addresses to manage. Your firewall manager would have your head. But you can get the Linux server's port 22 open.
Most UNIX/Linux users are very familiar with PuTTY and port tunneling. The idea is that you connect to the SSH port on the Linux server and log in successfully using client software that works like telnet. Once connected, you can have tunnels where the client on your PC will listen on a port and tunnel it through the SSH server, which will then connect to the host on the port you configure. An example: I configure a tunnel so that my PC's port 1080 is tunneled through SSH to port 80 on my company's intranet server. I then connect and login through SSH. Open up my web browser and enter the url: http://localhost:1080 This request goes through my SSH client, through port 22 on the Linux server, and then it will send the request to port 80 on the intranet server. The returned web page comes back the same way. Works like a VPN but you must map all tunnels you will use to each host directly.
The idea now is that you will setup your SSH client to map 3389 on your system, through the Linux gateway server, to your remote workstation or your Windows Terminal Server's port 3389. Once logged into SSH, you start the Remote Desktop client, point it at localhost, and you connect.
Except for some reason it doesn't work. You get an error like this:
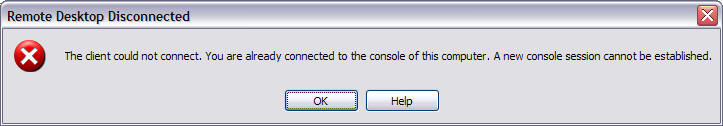
A while ago we ran into this issue and found a fix that was particularly ugly. You would copy the mstsc.exe and mstscax.dll files from system32 to another folder, and change the compatability mode properties on them to Windows 95. You can then connect to localhost. Why it works? Who knows. Except that while that works connecting to remote workstations and Terminal Servers initially, once the Terminal Server is moved into licensed mode it stops. This happens because the licensed TS connection requires a key that is written to the local clients registry. And in compatibility mode, you can't write to the registry.
Luckily, now with the newest release of PuTTY, a fix. You can, instead of mapping localhost (127.0.0.1) on your SSH client PC, you can now map other addresses. Such as 127.0.0.2. This is also automatically localhost, but the Remote Desktop Connection client won't give you an error. So you don't have to modify anything. Just map 127.0.0.2:3389 to your system on the other side of the gateway server's port 3389. Start the RDC and connect to 127.0.0.1.
I've written a script in WSH that front ends the entire connection. This uses the plink.exe command line version of PuTTY to make the actual connections. I have it included in the zip file for ease It will prompt you for your name, password, and then the name or IP address of the system you wish to connect to. If you haven't connected to that system before, it will make the initial SSH connection and automatically accept the SSH key. Then it connects, creates the tunnel, and sends a sleep 30 seconds command, and then an exit command to the remote SSH server. After it makes the connection, a few seconds later it calls MSTSC.EXE, which is the Remote Desktop Connection client name on Windows XP systems. The screen starts the connection, and assuming all is well, you're remote controlling the remote system. The sleep and exit command ensure that you don't have SSH tunnels laying around when you're not using it. It will not close the tunnel until you close out the Remote Desktop session. The script keeps a basic log of the SSH connection for troubleshooting purposes. There is no real error checking, since this is really simple. Therefore if you enter the wrong username or password, you'll just fail the connection. The password also isn't hidden while typing, that is a limitation of WSH. All you need to do is edit the connect.vbs script, and change the remoteGateway="ssh.gateway.system" line to be your Linux gateway server.
Hope this is a useful utility. It should work well enough for network administrators to give out to their normal users. And this is easier than manually reconfiguring your tunnel each time you connect to different hosts. If you make any improvements to the script, please let me know so I can include it in the distribution.