|
|
|||
 |
Department of Engineering |
| University of Cambridge > Engineering Department > Help > Network Support > Offsite Access |
Important: To increase security on a machine with Remote Desktop access enabled it is recommended that the network port that Remote Desktop connections use is changed from the default of 3389. An attempt to compromise a Windows machine will often target the default Remote Desktop Protocol (RDP) network port in order to try and gain login access, changing the default port helps prevent this type of attack, see:
The following procedure requires a Secure Shell (SSH) client. There are a number of SSH clients available to choose from, a free Win32 Telnet/SSH client that has been used successfully by many within the Department is PuTTY which can be downloaded here.
When you install and run PuTTY you will be presented with a configuration screen. Most of the configuration options can be left at their default, the important settings for connecting to a machine at Engineering and creating a port forward entry suitable for web proxy purposes are given below.
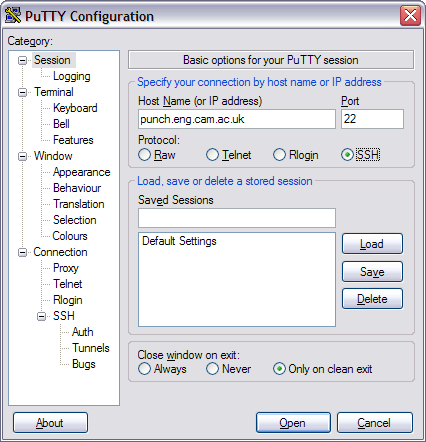
For external access to Engineering's hosts it is necessary to enter the fully qualified domain name of the machine you wish to connect to, for example punch.eng.cam.ac.uk, and select SSH for the protocol:
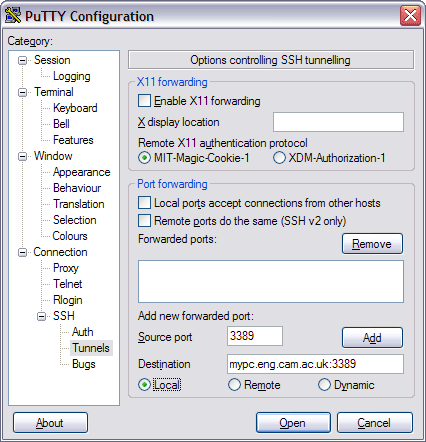
The next step is to create a port forward tunnel entry so that once the SSH connection is established any traffic sent to the local network port 3389 is redirected to the corresponding network port on your departmental desktop machine, mypc.eng.cam.ac.uk:3389, where mypc is replaced by your Engineering hostname:
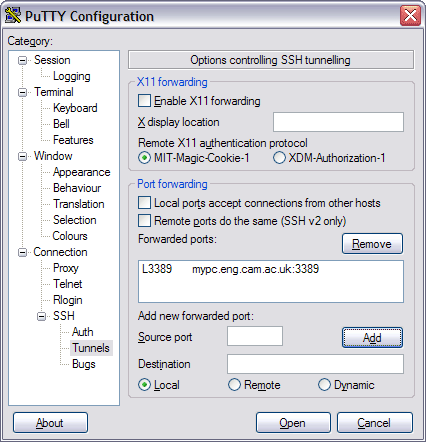
Click Add to include the forwarding rule in your PuTTY session:
In order to make life easier in future it's worth saving your PuTTY session so that it can be reloaded at a later date:

Creating a desktop shortcut whose target points to the location of the PuTTY executable followed by the name of the session to launch provides a quick and easy means to connect, for example:
"C:\Program Files\PuTTY\putty.exe" -load punch.eng.cam.ac.ukNote: The recommended Engineering infrastructure machines accessible from outside the University are:
club.eng.cam.ac.uk
punch.eng.cam.ac.uk
plane.eng.cam.ac.uk
The first time you connect to a machine using SSH you will be presented with a warning:
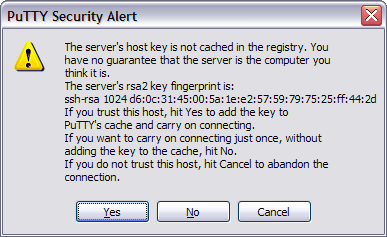
This is normal and if you don't want to see the same warning each time you connect you should click Yes. Next you will be prompted to enter your Engineering Teaching System userid and password:
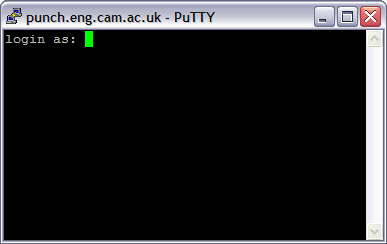
Once you have established the SSH connection you can minimise the PuTTY window.
Note: In order that the necessary network traffic can be forwarded over the SSH link to the remote computer PuTTY must be running with an appropriate port forward before trying to connect with the Remote Desktop Client.
The Remote Desktop Client software is pre-installed with Windows XP. If you are using a version of Windows other than XP you can download the client software here. By default the Remote Desktop Client is installed in Start, Programs, Accessories, Communications, Remote Desktop Connection:
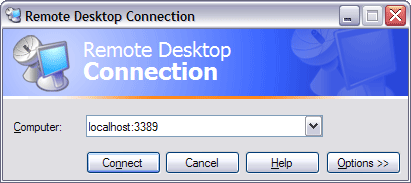
Clicking Connect at this point will forward Remote Desktop traffic from your local machine over the SSH connection back to your Engineering desktop machine. The Options button allows you to refine the way in which you connect and has settings for limiting the amount of network bandwidth used by choosing an appropriate connection type under the Experience tab. This can be useful when working over slow internet connections.
Windows XP Professional prior to Service Pack 2 does not allow local connections. The following workaround from Michel Toussaint, CCSE, MCSE (netshield@yahoo.com) can be used to overcome this limitation:
The limitation of Windows's XP Remote Desktop client is that it refuses any connection from the localhost (127.0.0.1) to the localhost with the following error message: "The client could not connect. You are already connected to the console of this computer. A new console session cannot be established". In order to be able to tunnel this through SSH, this limitation must be broken. The first idea was to hack the client executable and remove the limitation but it's simpler than that. I noticed that if you run the executable mstsc.exe from another operating system than XP, the limitation does not exist. Drilling a bit into that, it is possible to run mstsc.exe on Windows XP to the localhost by using application compatibility with older windows 9x. Procedure: 1. Create a folder (For example c:\TSclient) on your XP box 2. Copy mstsc.exe and mstscax.dll from your XP's %systemroot%\system32 to this folder. 3. Right click mstsc.exe and go to the properties of it. 4. Select the Compatibility tab 5. Check "Run this program in compatibility mode for" 6. Select "Windows 98/ Windows Me" 7. Click on OK 8. Connect your SSH to the remote network or machine 9. Forward another port than 3389, for example 3390 10. Use the newly copied mstsc.exe to connect to 127.0.0.1:3390 Notes: - You can connect to Windows 2000 terminal servers as well. - Do not forget to logoff from the remote XP. As Windows XP will allow only one session at a time.
Last updated: 30th January 2005
|
©
2006 Cambridge University Department of Engineering Information provided by network-support |